The focus of this research is to analyze the amount of privacy provided in Windows 10 when using the most restrictive privacy settings available. Windows 10 has been observed to establish encrypted connections to Microsoft servers without a direct related user interaction. softScheck already identified this traffic in an earlier analysis. Now our goal is to analyze the communication by monitoring the data being sent.
Contents
1. Setup
Since all telemetry communication is encrypted, we need to perform a man-in-the-middle attack. To do this we use a Raspberry Pi 3, which is a single-board computer the size of a credit card. Our focus is to identify and analyze the traffic of a Windows 10 client with the most restrictive privacy settings activated. Some Windows 10 versions (Enterprise, Education, and IoT Core editions) support an additional telemetry level, telemetry level 0: security. We use a Windows 10 Enterprise client (Version 1607 – Build 14393.447) and activate this level. In our setup, we use a newly installed Windows 10 Enterprise client without any additional software. The privacy settings are set to the most restrictive values according to the TechNet article Manage connections from Windows operating system components to Microsoft service. Our final Setup is shown in the following figure:
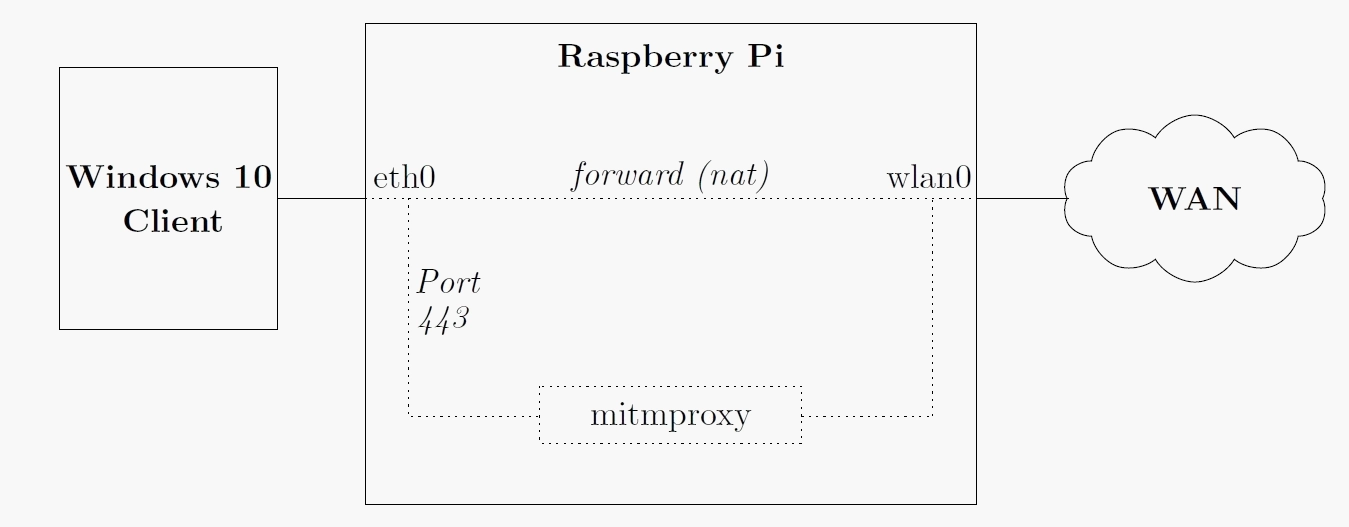
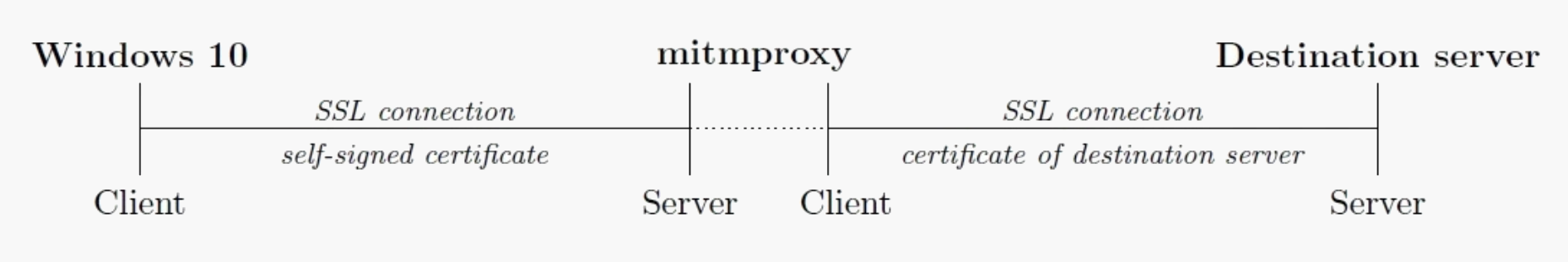
The open source Tool mitmproxy is used to perform the man-in-the-middle-attack. SSL traffic (port 443) is being redirected to mitmproxy while all other traffic is directly forwarded using NAT. To decrypt the encrypted traffic, we use mitmproxy’s built-in Certification Authority. To make this work, we import mitmproxy’s root certificate into our Windows 10 client. Now, mitmproxy behaves as a server to our Windows 10 client and establishes (as a client) a connection to the target server, as illustrated in the following figure. Bing Request Cookies
2. Findings & Evaluation
In an analysis of the recorded network packet traces we identified several connections to Microsoft servers. In general, there are two types of connections: Bing queries and telemetry data. A local search in the Windows start menu leads to multiple queries to bing.com. The complete search string as well as multiple prefixes of it are sent while you are typing. At this point, any connection to bing.com would not be necessary. Furthermore, the Windows 10 client repeatedly sends extensive telemetry data to Microsoft server. An overview is given in the following table:
| Server | Data |
|---|---|
| arc.msn.com | Telemetry data |
| arc.msn.com.nsatc.net | Telemetry data |
| bing.com | Bing queries + cookies |
| g.bing.com | Cookies |
| g.live.com | Cookies |
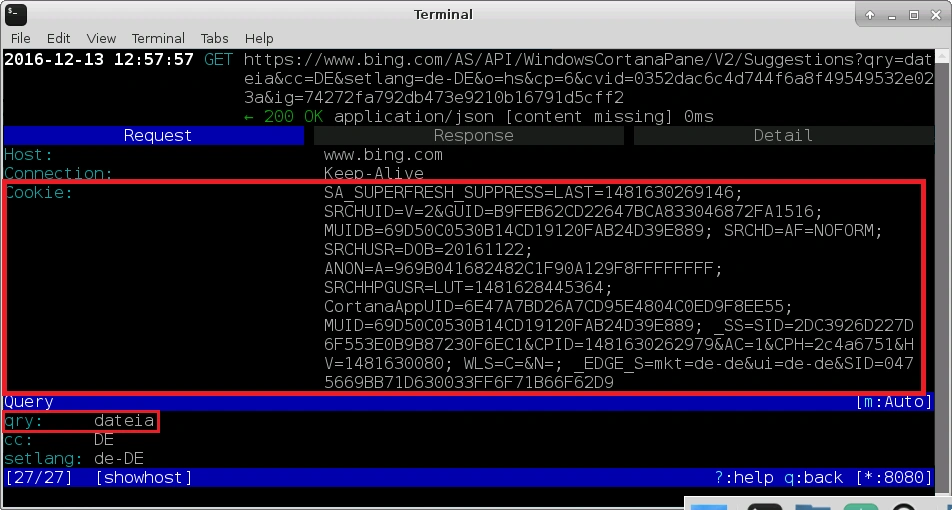
We identified the cookie Cortana AppUID in every query the Windows 10 client sends to bing.com. Since the Anniversary Update of Windows 10, the personal assistant Cortana comes built-in. Even with all adjustments in Cortana Settings > Privacy turned off, Cortana is still running in the background. Microsoft confirmed this behavior on its website about Cortana and privacy:
If you don’t sign in and don’t give Cortana permission to use your personal Cortana data, Cortana will still be there to help you search the web and your Windows device [..] and to perform other tasks that don’t require personalization. When you use the taskbar search box, you’ll start to get search suggestions as soon as you start typing or speaking. To do this, Windows sends what you type or say to the Bing service, which interprets it in real time to provide auto-suggestions. (Source: https://privacy.microsoft.com/en-us/windows-10-cortana-and-privacy)
Microsoft points out that, in this case, only services are made available that don’t require personalization. However, several unique cookies containing hash values were sent with the query as the following screenshot demonstrates. For this reason, it can’t be verified that queries stay anonymous. It is feasible for Microsoft to do a distinct identification with these cookies and the source IP.
As noted before, the identified Bing queries are triggered by Cortana. Due to the fact that all privacy-related settings were turned off (for maximum privacy), we did some further search. It is possible to deactivate Cortana completely. To do this, the key AllowCortana with the value 0 has to be added to the registry path:
HKEY LOCAL MACHINE\SOFTWARE\Policies\Microsoft\Windows\Windows Search
Users of Windows 10 Pro and Enterprise also have the opportunity to use a group policy. The group policy object Allow Cortana can be set in
Computer Configuration > Administrative Templates > Windows Components > Search
By using one of these settings the established Bing queries couldn’t be observed anymore.
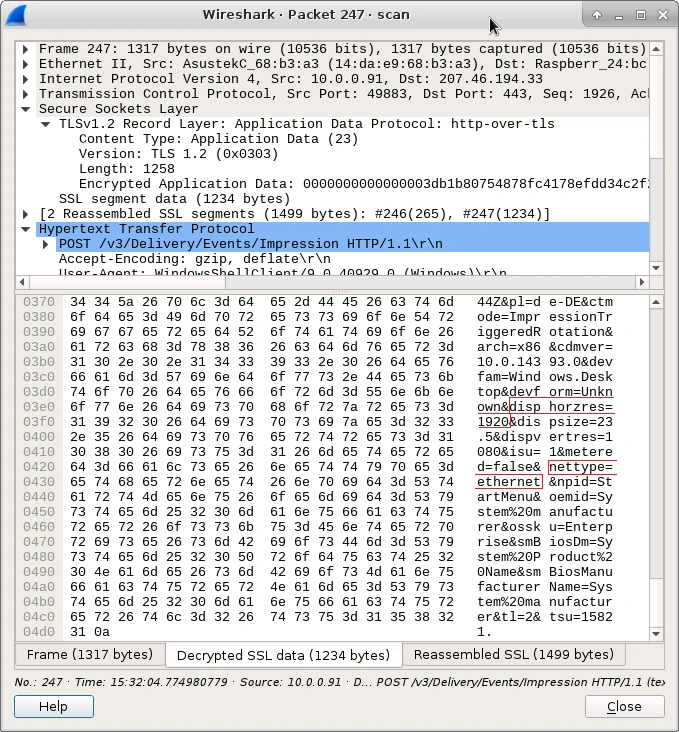
In addition to Bing queries, extensive telemetry data are transmitted. Besides multiple identifiers, data points such as display resolution and the type of network connection are transmitted, as the following screenshot indicates:
3. Conclusion
As has been shown, undesired traffic of Windows 10 can be limited to a certain extent, which makes it feasible to use Windows 10 in a corporate network. It has to be considered that the telemetry level Security (0) is only available in Windows 10 Enterprise, Windows 10 Education, Windows 10 Mobile Enterprise, Windows 10 IoT Core (IoT Core) and Windows Server 2016. All other Windows Versions are limited to the telemetry level Basic (1).
According to Microsoft, additional data about “Health & Quality” are gathered at this level. However, regardless which adjustments are set, you have to keep in mind that Windows 10 still sends telemetry data. As an easy way of managing all privacy related adjustments (including complete deactivation of Cortana) is offered by the tool DisableWinTracking.
Read about other interesting topics on our blog.