Microsoft Azure and Cloud-Services unrestricted open for attacks
12An unauthorised signature key (created in 2016 - expired 2021) was used as a master key to give unauthorised persons full access to the Azure Cloud and cloud-based services! The perpetrators had access (probably for years) to presumably all Microsoft cloud applications such as ExchangeOnline, Office365 with Outlook.com, Sharepoint, Onedrive and Teams - as well as third-party applications with the "Sign in with Microsoft" function. Microsoft has so far published little on the case and has not (fully) named the affected products, so users can hardly protect their data so far.
Almost two years ago, a security vulnerability in the Microsoft Cloud Azure was exploited to access such primary keys and thus gain (unauthorised) full access3. Although the vulnerability was patched after 14 days, not all of the several thousand users worldwide were informed and - as in the current case - neither about the necessary security measures nor about the remaining risks. At the time, the incident was rated as the "worst cloud vulnerability imaginable"4. The current case surpasses the old one.
In January 2021, it became known that attackers were able to penetrate Microsoft's internal network and view source code5 via a backdoored version of SolarWind's "Orion"6. In addition, critical vulnerabilities7 in the printer administration were not patched for a long time. The extent to which these attacks are the basis for more recent attacks has also not been published.
In the following, the current event is presented and evaluated - as far as the technology is known and facts are published. Overall, Microsoft is accused of being too hesitant to inform and not making the significance of the case sufficiently clear. Industry-typical (cloud) errors are also discussed and what security measures cloud users can take.
In the following, the current event is presented and evaluated - as far as the technology is known and facts have been published. Overall, Microsoft is accused of being too hesitant to inform and not making the significance of the case sufficiently clear. Typical (cloud) errors in the industry are also discussed and what security measures cloud users can take.
Healthcare, energy, food, media, communica-tions and finance are likely to be particularly affected.
1. What has happened so far?
In mid-June, a US government agency detected unauthorised access to your emails in online Exchange accounts; these also affected European government agencies8. It is not known how long the perpetrators had been active in Microsoft systems at that time.
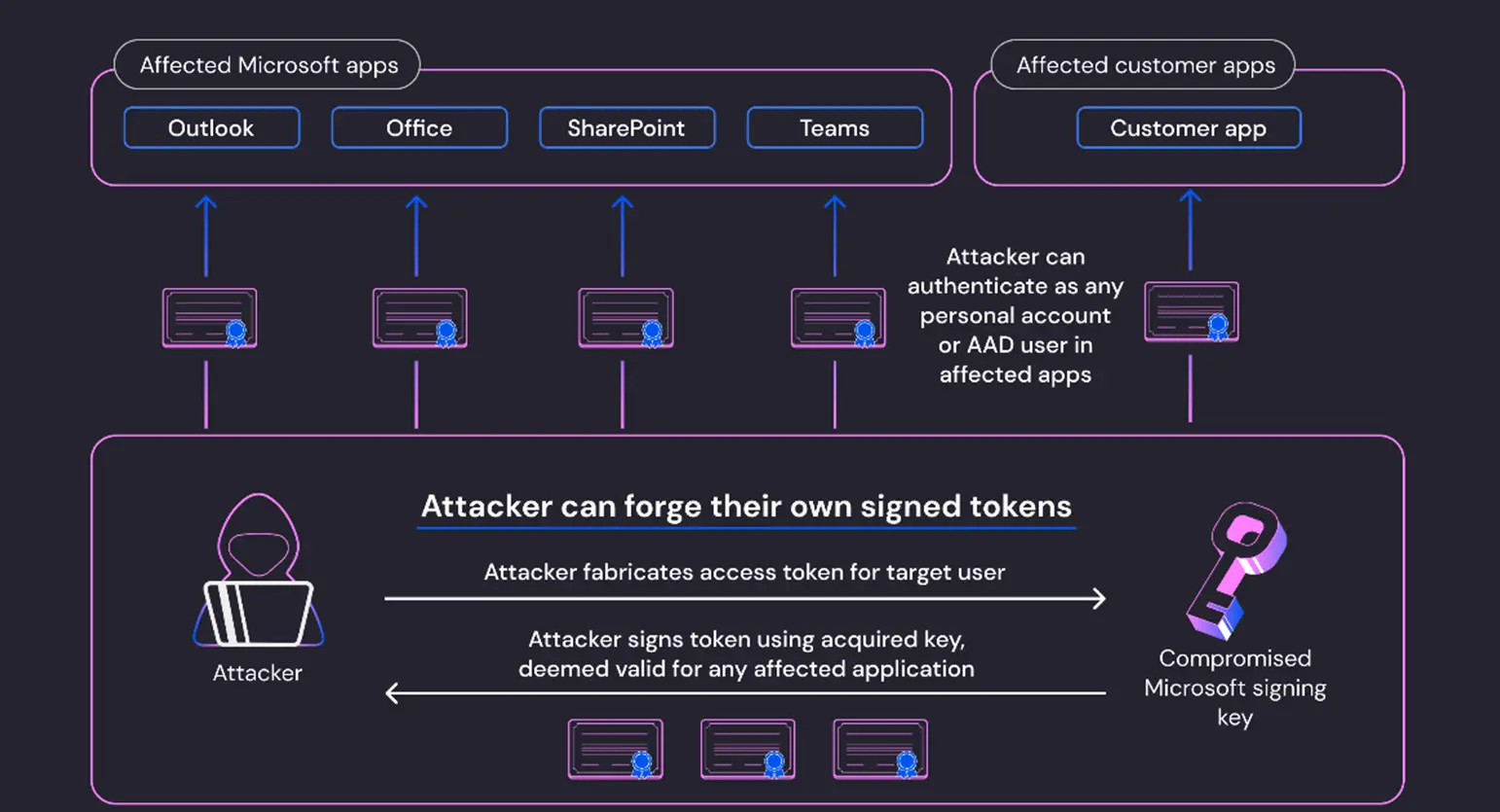
The US cloud security company Wiz10 has (according to its own information) meanwhile identified the signature key used by the perpetrators with the help of the fingerprint published by Microsoft. This was used to generate access permissions and spy on mails from companies and government agencies. It is unpublished when, where and how the perpetrators were able to read and copy the signature key, and it is also unpublished how the validity check could be bypassed.
Overall, there appear to be several design flaws in the access control. This leads to the assumption that the perpetrators were active in the Microsoft systems for a long time and carefully scouted out and also tried out possible attack paths. Worldwide, perpetrators of cyber attacks are active in the victim systems for an average of 6 months.
Microsoft has taken initial security measures and blocked the use of the signature key and the tokens generated with it and the perpetrator activities. The signature key has been replaced.
2. Who were the perpetrators?
At this point in time, a verifiable assignment to a state (China) and/or to a cyber-crime group (Storm-0558) is not yet possible; names or assignments cannot be verified. Intelligence experts assume that Microsoft is deliberately naming names and nationalities in order to divert attention from its own mistakes and to reassure the public and governments.
Even if evidence were available, prosecution of the perpetrators would be very costly - although this has been achieved in individual cases in the USA.
3. Who are the victims?
All companies and authorities worldwide that use the Azure Cloud or Azure Cloud Services.
4. What mistakes were made?
It is an OpenID signing key for the Azure Active Directory (Azure AD or AAD). This is the Microsoft cloud directory service. A signature key for the creation of digital signatures was copied without authorisation, which generated a digital signature that was actually only intended for private customer accounts (MSA) also in the Azure Active Directory for business customers. A justification for this decision is (so far) unpublished.
Presumably, this key is also known to security authorities; it may not have been correctly secured there.
5. Evaluation - what are the risks?

When (finally) the attack is completely (!) analysed and published (?) and the points of attack, the exploited vulnerabilities are published and patched, this attack is not yet repelled! The perpetrators were able to install backdoors undetected in all systems of all customers, in all software, firmware and (according to experience) also in microcode of devices (!), which they can access undetected in the coming months and years and read out (espionage) or manipulate (sabotage) data in the systems of all affected companies and authorities.
6. Recommendations to Microsoft
The 'Secure Development Lifecycle (SDL)' developed by Microsoft employees Steve Lipner and Michael Howard11 should already be used in the first development steps. It forms the basis for the ISO/IEC 27034 standard (Application Security)12. According to the state of the art, the security architecture includes storing important data such as signature keys in a hardware security module (HSM), which should provide protection against copying and manipulation.
Microsoft should promptly recommend security testing and security measures to its customers.
7. Recommendations to users
Users should, for effective mitigation, implement a minimum set of security measures that achieve reasonably secure use DESPITE insecure clouds: Reduction of attack surfaces as well as the (few) security checks recommended by Microsoft13.
It is already advisable to implement the security measures recommended in European laws and directives such as the Digital Operational Resilience Act (DORA) and the Network Information Security 2 (NIS2) directive.
Clouds themselves cannot be 100% secured! The minimum measures therefore include encryption of the data stored in the cloud. The (unencrypted) processing of valuable company data in a cloud always appears to be risky.
If personal data could be affected, the responsible data protection authorities should be informed promptly as a precaution.
Users should first identify the points of attack (vulnerabilities) exploited by the perpetrators and also the (from experience in the meantime) installed backdoors. This can be done well with a complete security test (not only penetration test) - even if Microsoft states that "no customer action is required" and "if you have not been contacted, our investigations indicate that you have not been impacted". Furthermore, it is essential to check every AAD and Microsoft account for unauthorised activities. Politically, it would be desirable to grant users the right to security check products such as clouds - i.e. also with other cloud providers.
The more explosive the case actually is, the more the impression arises that the implemented security functions are compromised, the greater the interest of Microsoft and the security authorities in keeping details secret. So we won't learn much more.
-
Wilfried Kirsch, Handelsbevollmächtigter softScheck GmbH, Köln – St. Augustin Wilfried.Kirsch@softScheck.com ↩︎
-
Prof. Dr. Hartmut Pohl, geschäftsführender Gesellschafter softScheck GmbH, Köln – St. Augustin Hartmut.Pohl@softScheck.com ↩︎
-
https://www.heise.de/news/Cloud-Datenbank-GAU-Microsoft-informiert-Azure-Kunden-ueber-gravierende-Luecke-6176601.html ↩︎
-
https://www.golem.de/news/cosmos-db-tausende-azure-nutzer-von-sicherheitsluecke-betroffen-2108-159178.html ↩︎
-
https://www.softscheck.com/en/publications/2021/der-patch-ist-der-angriff/ ↩︎
-
https://www.heise.de/news/PrintNightmare-Schon-wieder-eine-Drucker-Luecke-in-Windows-ohne-Patch-6163743.html ↩︎
-
https://www.heise.de/news/Neue-Erkenntnisse-Microsofts-Cloud-Luecken-viel-groesser-als-angenommen-9224640.html?wt_mc=nl.red.ho.ho-nl-daily.2023-07-25.ansprache.ansprache#nav_das_cloud_fiasko_0 ↩︎
-
https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr ↩︎
-
https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr ↩︎
-
https://learn.microsoft.com/de-de/security/operations/token-theft-playbook ↩︎